Two main categories of emails are sent: those that complain about serious issues regarding a recent stay, and requests for information to assist a future booking. Both typically necessitate a fast response from hotel management.
Complaint emails can range from allegations of violent or prejudicial behavior from staff or having possessions stolen, for example. In these cases, attackers will often compose a strongly worded email, only including text, outlining their initial complaint.
When the staff then responds by requesting more information, the attacker sends a message directing the staff to open a link that supposedly contains evidence supporting their claim.
These links typically point to legitimate cloud storage services like Google Drive and contain a password-protected archive, the password for which is included in the email, which leads to the download of a digitally signed executable. That program contains the credential-stealing malware, which starts up when the worker opens the file thinking they're about to view a document.
The executable is typically large, like 600MB in size, to perhaps fool or put off antivirus scanners; the password protection on the archive also obscures the contents from scans until it's unpacked. The actual malicious code is all the way at the end of the executable file, and seems to be a variant of the Redline Stealer or Vidar Stealer Windows malware.
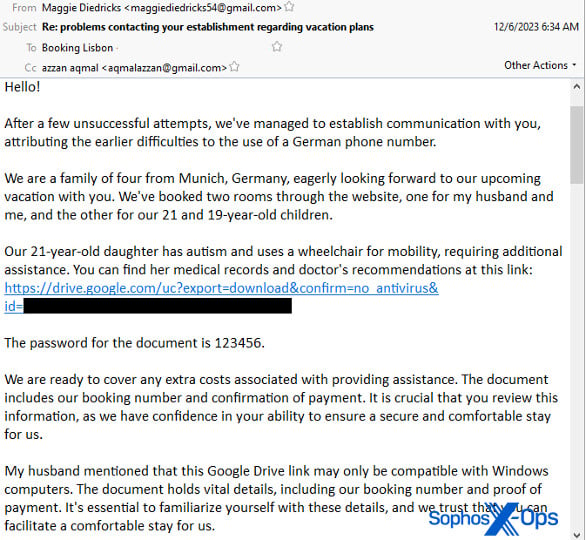
Example of an attacker's email sent to hotels including a link to a malicious archive instead of medical records. Image courtesy of Sophos
Attackers are also known to pose as guests traveling with disabled children. Similar to the previous examples, the attacker will instruct the staff to visit the link, which supposedly contains the information necessary for the hotel staff to familiarize themselves with the medical needs of their fake children.
Some emails are composed in what reads like native English, reducing the likelihood of staff members working fast-paced jobs being alerted to the malicious nature of the message. Others included the grammar and lexical errors one would expect from a phishing attempt.
Hotel staff have been advised to make themselves aware of the types of scams going around and be vigilant to any signs that the email might be an attempt at an attack.
Other methods involve creating an emotional scenario claiming the need for the hotel's help to retrieve a lost item left behind in a hotel room, for example – sometimes with sentimental value.
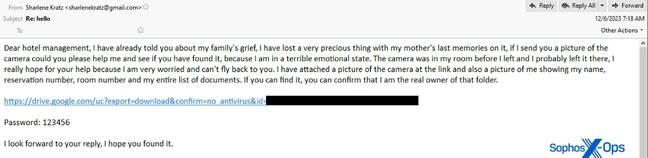
Email sent to hotels including a link to a malicious archive instead of images of a lost item. Image courtesy of Sophos
This could be anything from a passport needed to fly home, a camera containing the last images of a deceased relative, or something else of the like.
In these cases, attackers may try to disarm the staff with grief, playing on their willingness to offer help, which Sophos says is a self-selecting trait of successful hospitality workers.
When the hotel staff asks for reservation details (name and booking number), the attackers' attitude turns from grief to mild aggression, responding with a message akin to: "I have already told you about my family's grief, I have lost a very precious thing with my mother's last memories on it, if I send you a picture of the camera could you please help me."
Again, the message then contains a password-protected download link that leads to malware.
All of the methods described in the research serve to steal hotel management credentials, which have recently been used in a spate of attacks against Booking.com customers, and have been ongoing since at least March 2023.
- Philippines, South Korea, Interpol cuff 3,500 suspected cyber scammers, seize $300M
- Millions of Xfinity customers' info, hashed passwords feared stolen in cyberattack
- FBI develops decryptor for BlackCat ransomware, seizes gang's website
- Qakbot's backbot: FBI-led takedown keeps crims at bay for just 3 months
The goal is to steal credentials to admin management portals, which are in turn logged into the Booking.com partner portal.
From there, attackers have been sending messages directly to customers from within Booking.com, lending an air of legitimacy to the communication. Conversations even follow on from existing chats from within the travel company's app, for example.
Credit card details are requested to secure a customer's booking, while also being told it will be cancelled within 24 hours if details aren't provided – creating a sense of urgency. From there, predictably, money is being siphoned from the stolen payment details.
When the activity was first observed, it led customers to believe Booking.com's own systems had been compromised, but investigators managed to uncover the true nature of the incident.
Investigating the incident, Secureworks also spotted a high demand for Booking.com credentials on underground forums, with some users offering up to $5,000 for a valid infostealer log, along with incentives to regular suppliers.
One crook – who offers a service that checks infostealer logs for valid credentials to various platforms, including Facebook Ads Manager, Gpay, Discord, and more – added a new Booking.com admin portal service to the offering, again suggesting demand has risen.
A Booking.com Spokesperson told The Register:
We are aware that some of our accommodation partners have unfortunately been targeted by phishing emails in recent months that are deployed by criminals using a host of known cyber fraud tactics, which ultimately encourage them to click on links or download attachments outside of our system that enable malware to load on their machines and in some cases, lead to unauthorised access to their Booking.com account. While this breach was not on Booking.com, and numbers of accommodations impacted by these phishing attacks represent less than a small fraction of a percent of the accommodations on our platform, we understand the seriousness for those impacted, which is why our teams work diligently to support our partners in securing their systems as quickly as possible and helping any potentially impacted customers accordingly, including with recovering any lost funds.
Phishing attacks and online fraud continues to be a pressing issue across many sectors, including the travel industry, which is why we continue to make significant investments to limit the impact of these ever-evolving tactics as much as possible. Due to the rigorous controls and the machine learning capabilities we employ, we are able to detect and block the overwhelming majority of suspicious activity before it impacts our partners or customers. We have also been sharing additional tips and updates with our partners about what they can do to protect themselves and their businesses, along with the latest information on malware and phishing so that they are as up to date as possible on the latest trends that we’re seeing.
In terms of some practical steps that customers can take to remain safe online, we recommend vigilance and that people carefully check the payment policy details outlined in their booking confirmation. If a property or host appears to be asking for payment outside of what’s listed on their confirmation, they should reach out to our customer service team for support. Also, it's good to remember that no legitimate transaction will ever require a customer to provide their credit card details by phone, email, or text message (including WhatsApp).
"While this breach was not on Booking.com, we understand the seriousness for those impacted, which is why our teams work diligently to support our partners in securing their systems as quickly as possible and helping any potentially impacted customers accordingly, including with recovering any lost funds," it told the BBC.
A follow-up piece from the BBC showed how customers lost hundreds of pounds through the Booking.com scams. The company said it was implementing new safety features but said that there was no "silver bullet to eradicate all fraud on the internet." ®


